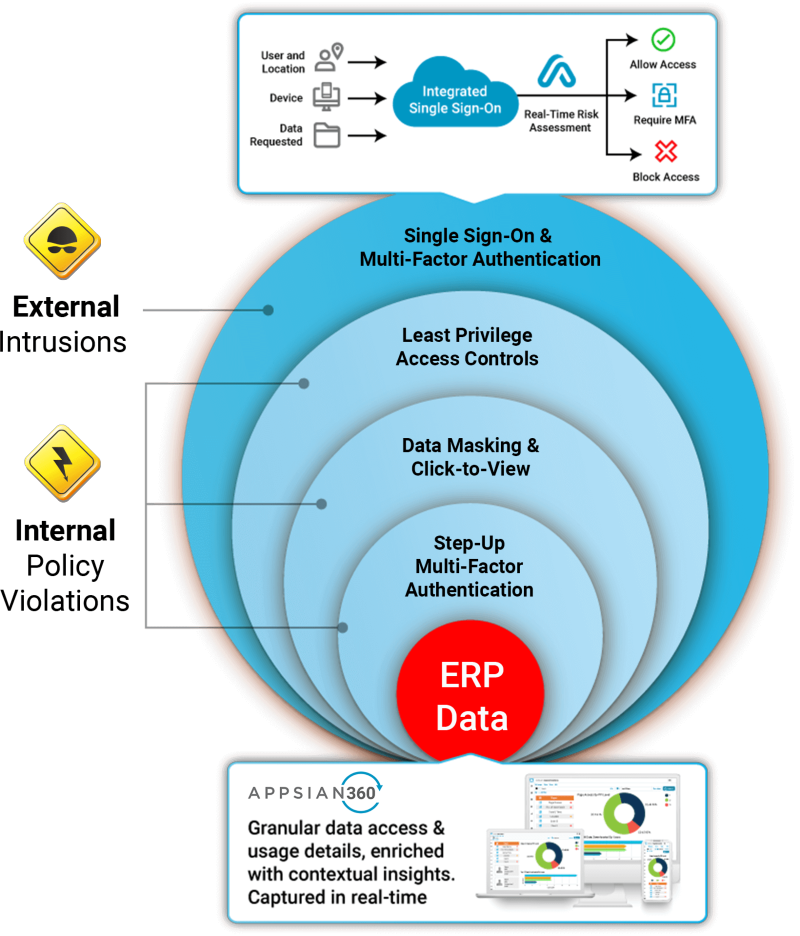
As work-from-home continues into 2021 indefinitely and the reality of this increased risk becomes clearer, organizations should heavily prioritize the modernization of their existing business applications – especially legacy ERP applications like PeopleSoft. Mainly because native user authentication, governance, data privacy and visibility features can leave an organization open to a myriad of risks. This has opened the door to organizations scoping a defense in depth strategy.
When you hear the term defense in depth, you typically think about traditional information security measures like network security controls, antivirus protection, database monitoring, and more. IT and security teams realized that multiple layers of security are necessary across the enterprise because cybercriminals will find vulnerabilities somewhere. Sadly, some of the most costly vulnerabilities for organizations using PeopleSoft ERP applications have proven to be the users themselves (employees, 3rd party vendors, students, etc.) It’s no secret that making these applications available on the open internet has introduced risk, so we frequently get the question, “how can I apply defense in depth to my PeopleSoft users?”
Step 1: Integrate your Identity & Access Management
This would be integrating your single sign-on and multi-factor authentication natively with PeopleSoft and your identity provider. Using proxy servers or customizing PeopleSoft poses their own risks and complexity, which is why using a native SAML handler (like Appsian) is a best practice. This minimizes the possibility of corruption, and a configurable solution(s) will scale much more effectively.
Integration of multi-factor authentication also enables stepped-up authentication, so users can be forced to re-authenticate once they have already passed the login screen. This should be applied to highly sensitive transactions like editing a direct deposit account number, accessing compensation data, or running a report containing employee PII.
Step 2: Apply Dynamic Authorization in Accordance with the Principle of Least Privilege
Controlling data access for high privilege PeopleSoft users can be challenging because native authorization is basically “all or nothing.” Limiting access to superfluous data or limiting access based on location/device/etc. is simply not an option. Leaving the door open to enormous risk. We have discussed time and time again that the context of access often defines risk, and this is never more true when users can access the system remotely.
Using a dynamic rules engine, Appsian can take the contextual variables of a user’s access and define privileges in real-time. Thus, mitigating risk. Don’t think a user needs access to compensation data from an unmanaged device or certain location? Want to limit the access granted to users or 3rd party vendors at certain hours of the day? Then dynamic authorization is the solution for managing that risk.
Step 3: Mask Sensitive Data Fields (Partial, Full, or Click-to-View)
This is data privacy 101, and as regulations like GDPR and CCPA become the norm (with wider federal guidelines likely coming soon), masking sensitive data is table stakes. After all, with PeopleSoft systems housing a wide range of PII, much of which belongs to past or prospective users (not just current employees), there is a treasure trove of personal data that comes with a far greater holding cost than you might realize. Masking data at the UI level at least ensures that those accessing the applications either in an authorized or unauthorized manner do not have needless access to valuable data through various pages, reports, or queries.
Step 4: Monitor Data Access & Usage
Monitoring the data users are accessing is not possible in PeopleSoft without enhancing logging and analytics capabilities. Having greater visibility cannot be overstated, and having a direct view of how data is accessed is one of the most valuable pieces of defense in depth. After all, in a sea of every day, authorized activity – how likely are you to detect the subtle hints of unauthorized activity? Phishing and privilege misuse are the main enemies of any data loss prevention strategy. The best way to detect and respond to unauthorized activity is through an analytics platform specifically designed for ERP applications, like Appsian360.
Step 5: Contact Appsian
To learn more about how you can apply Defense in Depth to PeopleSoft, contact us at info@appsian.com.
Figure 1: Prevent external and internal threats with defense in depth from Appsian.