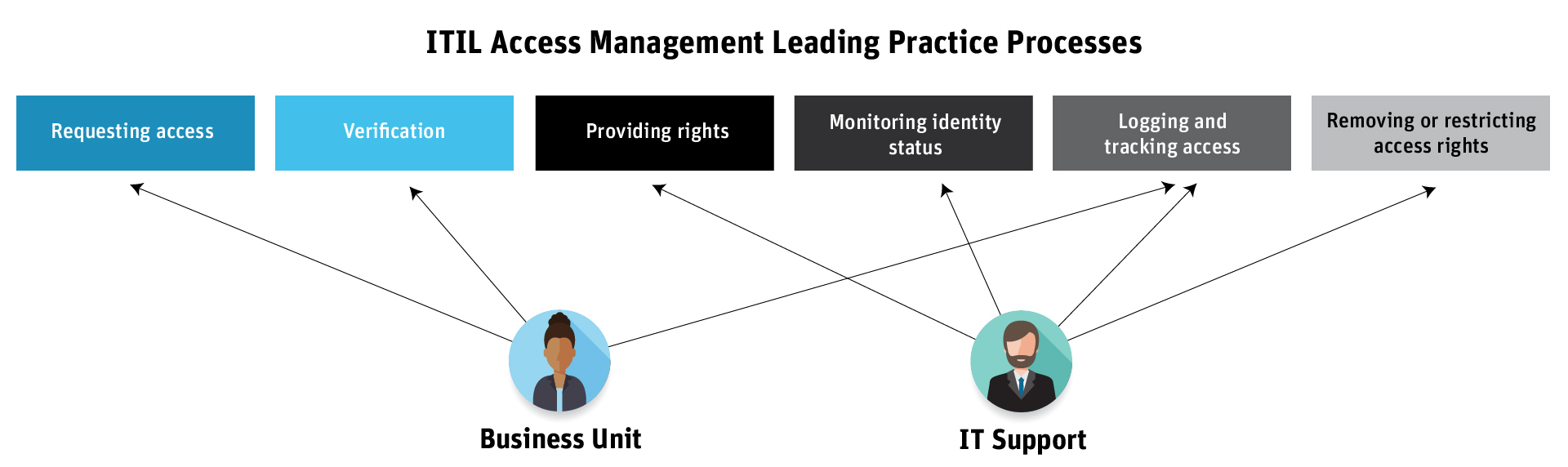
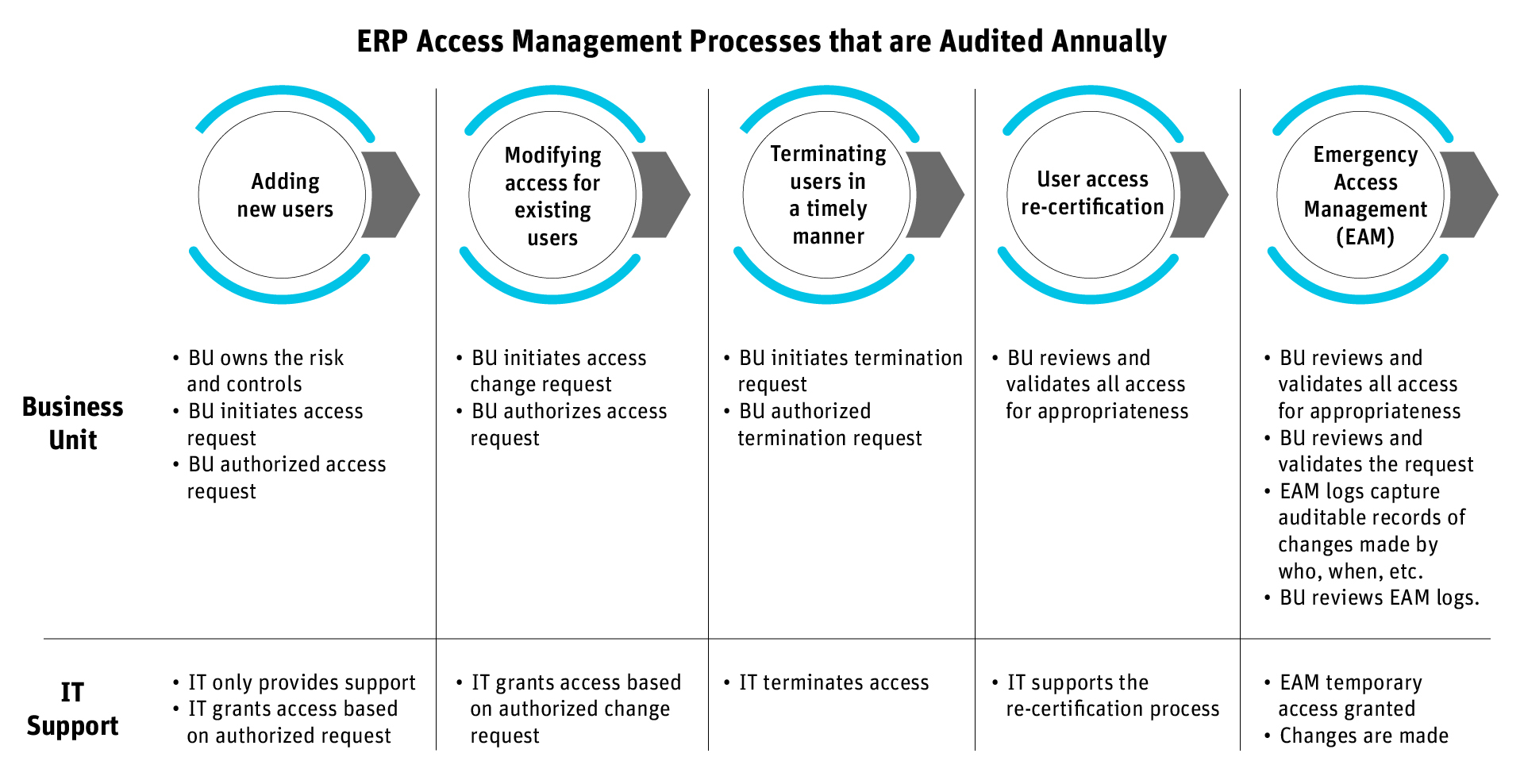
Organizations that use ERP applications like SAP, PeopleSoft, Oracle EBS, etc., manage thousands of users. Most of these users have limited roles that only allow them to perform their job-related tasks. But there exists a subset of users/accounts who are granted a wide spectrum of authorizations because their role entails managing the application itself: privileged users.
From an operations point of view, these roles are essential for the day-to-day functioning of the application to support the business. However, from a security perspective, the level of access and authorization granted to these privileged user accounts increases the overall risk exponentially. In fact, Forrester estimates that 80% of data breaches have a connection to compromised privileged credentials, such as passwords, tokens, keys, and certificates.
Who are Privileged Users?
Privileged users are users who are assigned roles and authorizations to perform functions that go beyond regular business transactions. These users include database administrators, network engineers, application developers, or third-party consultants. Their user accounts possess enhanced permissions that allow them to access sensitive data or modify key system functions. Also referred to as Superusers, some of the overarching privileges extended to them include:
- Full authorization to read, write and execute
- Creation or installation of files or software
- Modification of files and settings
- Deletion of users and data
Security Implications of Privileged User Accounts
Privileged users have a high level of access which means they will always be a target for attackers. If these accounts are compromised, it will lead to attackers gaining the same level of access.
Once inside, attackers can move from system to system undetected without leaving any digital footprint, making it harder to detect and stop. In addition, the attackers could gain access to an organization’s sensitive and confidential data, including company trade secrets.
If misused, either because of an error or with malicious intent, privileged user accounts can also inflict grave damage to a system or organization. Companies may have adequate security to prevent external threats, but privileged users are already inside the system. They can create backdoors, delete or modify data, override security settings, and more without detection.
According to the IBM 2020 Cost of Insider Threat Report, the average cost of an insider threat almost triples from $3M to $8.7M if the incident involves an imposter or thief who steals credentials and the costliest type of credential theft involves the theft of privileged users’ credentials.
Mitigating Privileged User Risk
Privileged users are granted greater access rights for a reason. They maintain and update applications that are critical for business operations. They are also responsible for a range of functions that require access to multiple servers, modules, and/or databases. This access also significantly increases the organization’s overall risk. However, this “privilege” can be counterbalanced with security measures that do not overly restrict them from performing their tasks.
Enforce Least Privilege Access
Many ERP applications provide role-based access controls and role-based authorizations. This means any user who logs in with valid credentials is granted all roles and authorizations assigned to that account. Thus, when a privileged user’s credentials are compromised, the attacker essentially becomes a privileged user giving them unchecked access.
However, by implementing attribute-based access controls (ABAC) through a dynamic policy engine, access can be allowed based on contextual attributes like location, time range, days, security clearance level, IP address, and more. For example, restricting privileged users to access only via your secure network ensures attackers cannot log in through an unknown network – significantly mitigating your risk while alerting you to failed access attempts.
Enforce Segregation of Duties (SoD)
Privileged user roles and authorizations should be regularly audited to ensure that they only have authorizations that are needed to perform their jobs. If the privileged user has not utilized a particular role within a specific timeframe, organizations should consider removing those privileges from the user. Since the user has never performed such functions before, they would not miss those privileges.
Even in cases where special privileges have been granted to perform specific tasks, a time limit should be set after which access is automatically revoked. These steps ensure that privileged users only have the necessary access at any given time and limit the organization’s overall risk.
Implement Step-Up MFA For Privileged Users
While your organization may have MFA at the login level, deploying step-up authentication for sensitive transactions at the page and data field level ensures that access to data and transactions is allowed only after the user has re-authenticated themselves.
Adding additional layers of authentication not only improves your security posture but also creates logs that can be monitored for suspicious activities. For example, a privileged user who is authorizing payment transactions can be easily identified during an audit since the user does not belong to the payroll or procurement team.
Behavior-based Profiling
Monitoring administrator accounts can help identify when one is compromised. However, large organizations may have hundreds of privileged users, and manual monitoring is virtually impossible. This is why Appsian Security’s unique algorithm combines multiple data sources to create a joint profile for each employee, including privileged users. The solution uses this business profile as the basis for optimization and as the behavior baseline.
This method is subsequently used to analyze irregular behavior, unused activities and authorizations, recommended authorizations for roles, and unoptimized license types. Privileged users who deviate from their normal usage can be easily monitored. For example, an anomaly is created when an SAP administrator who never accessed the customer database before tries to access it. Even though the user has the authorization to access the database, a deviation in behavior can be an indication of compromised credentials, giving security teams an impetus to check user behavior.
The IBM 2020 Cost of Insider Threat Report states that 29 percent of all credential thefts involve the theft of privileged users’ credentials. This proves that privileged users are primary targets for attackers because of their access privileges. Appsian Security mitigates the risk of high privilege credentials and sessions being exploited by bad actors by enabling you to implement multiple security measures like attribute-based access controls, step-up authentication for sensitive transactions, segregation of duties, and behavior-based profiling.
Schedule a demo with our security experts to find out how privileged user risk can be mitigated across your ERP ecosystem.