When Business Policies & Internal Controls Misalign, You’re Left with Risk
Tight business process controls that are well aligned with business policies leave minimal tolerance for risk. Unfortunately, these business policies cannot always be met with legacy ERP controls. As business becomes more dynamic, access expands beyond the local office, and regulatory requirements grow, many organizations are finding a gap between governance goals and internal control capabilities.

This “controls gap” is a misalignment that results in risk. And its impact is far reaching. On average, organizations face a 5% loss of annual revenue from fraud, theft, and error – with insufficient controls being the key reason. Executive confidence suffers, and inefficient business processes can hinder the bottom line. For IT leadership, you’re left with a higher level of risk associated with your ERP applications. With a myriad of transactions taking place in real-time, focusing your risk management strategies on data, rather than static roles and permissions, is critical.
Limitations of Traditional Security Controls
-
Static Security Policies
Static, role-based security controls pose limitations that can force compromise between security and business policies. Unable to fully address risk with static controls, business owners will forego desired access policies or be forced to rely on manual processes to mitigate risk.
-
Uncapped Financial Fields
While editing or altering some low-risk data fields can be harmless, repeated edits can jeopardize the integrity of a financial transaction. Traditional ERP controls do not allow organizations to easily limit or block access based on the monetary value of transactions – resulting in a drastic increase in business risk.
-
Manual Business Risk Controls
Organizations are overly reliant on manual controls to mitigate business risks. When you cannot address risk with automated controls, someone must manually gather, review, and address any potential violations. This process is slow, diverts time from regular duties, and can lead to violations being missed.
-
Time-Consuming Audits
Uncovering business risks often rely on manual and time-consuming audits and reports. Since it can take weeks to months to complete an audit, malicious activity can go undetected between review cycles. Furthermore, the immense amount of manual effort involved can limit the scope of a review, potentially allowing risk to remain hidden.
Enhance Existing Role-Based Access Controls (RBAC) With Attribute-Based Access Controls (ABAC)
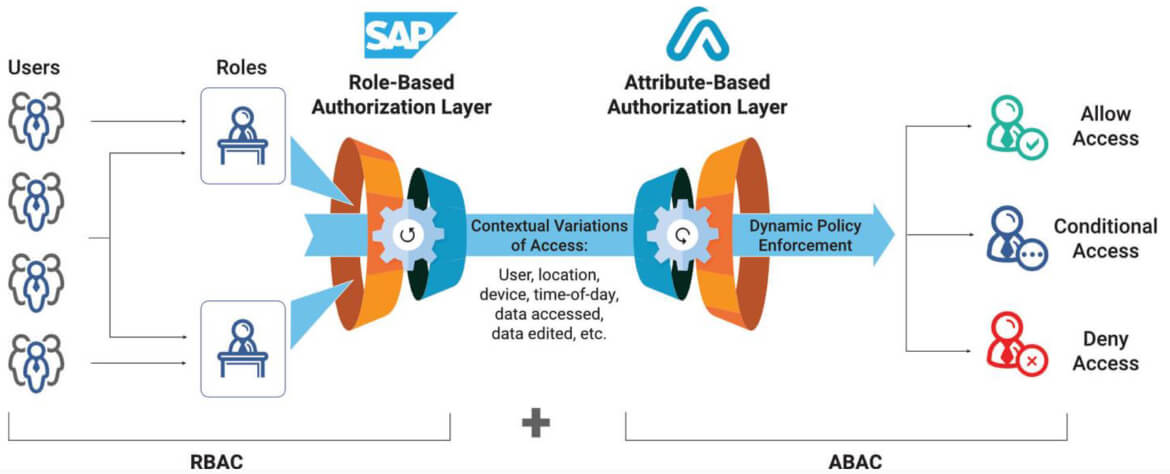
Strengthen Business Process Controls with Data-Centric Security and Continuous Monitoring
-

Improve Alignment Between Controls and Business Policy
Enforce preventive controls that have the granularity to align with business rules. Using Appsian’s Policy-Based Access Controls, you can restrict access to sensitive data and transactions based on attributes such as: activity type, IP address, user location, time of day, amount of money transacted, the number of transactions, user activity trends, SoD policy and more.
-

Cap Financial Exposure in Financial Transactions
Leverage data-centric security controls to set tolerances in financial transactions appropriate to the associated risk. Appsian allows you to cap the monetary value of a transaction, set limits on how many times a field can be changed, or set percent variance controls on field-value changes. Organizations can limit the financial risk of specific transactions by using rate-limiting controls.
-

Uncover Business Process Risks in Real-Time
Detect, measure, and monitor business risks with Appsian360’s Continuous Monitoring capabilities. High-fidelity insight into user & transaction activity, data-attributes (from within transactions), and access context (from the network level) provides a holistic picture to help you identify anomalous activity and enable faster decision making if the integrity of a transaction is in question.
-

Streamline Audits
Appsian’s Real-Time Analytics allows organizations to eliminate most of the time-consuming work of auditing business processes in search of fraudulent activity. Using the analytics dashboard, audit teams can view transaction detail to quickly identify suspicious activity and immediately begin the remediation processes. With Appsian, your teams can spend more time actively preventing risks vs. manually trying to uncover them via audit.
PREVENTIVE CONTROLS
- Prevent GL entries from being manually changed after hours
- Impose a rate-limiting control on the dollar amount of XYZ transactions
- Control excessive discounting (e.g. +/- 10%)
- Limit the number of times a transaction can be performed in a specific time period
- Control transaction authorizations based on a user’s transaction count and/or the cumulative value of these transactions over a specific time period.
DETECTIVE CONTROLS
- Capture event alerts for transaction activity that violates pre-defined business rules.
- Detect business process activity that deviates from normal baselines.
- Continuously monitor high-risk transaction activity
- Detect anomalous activity originating from abnormal locations, networks, or time of day.
Unique Benefits of Appsian:
Maximize your ERP investment & modernize legacy applications to meet current business requirements.
Streamline risk management with greater control and visibility over data access.
Extend ERP access beyond the firewall & provide data governance using dynamic, fine-grained access controls.
Lightweight & quick-to-deploy solutions that natively integrated into the ERP web server without requiring customizations or additional hardware.