Legacy ERP Systems are Susceptible to Insider Security Threats
Insider security threats are becoming more frequent and more costly to organizations. According to the Verizon Insider Threat Report, 57% of data breaches are caused by trusted insiders with access to sensitive data. The Ponemon Institute calculates the average cost per insider incident is $11.45 million. The privileged access and knowledge of company operations make insider threats one of the most common yet elusive risks to manage. Not all insiders are disgruntled employees, and their motivations, intent, and access levels vary. Regardless of who they are, an insider who intentionally or unintentionally violates a business or security policy can inflict plenty of damage. Legacy ERP applications were not designed to help you detect insider threats.
Limitations of Traditional Security
- Security teams struggle to determine the difference between regular user activity and anomalous activity.
- Access governance is challenging in remote environments due to users accessing from unknown networks.
- Insiders usually know how to bypass controls and violate security policies without fear of being discovered.
- Legacy ERP applications lack the ability to provide granular insights into user activity.
- Native ERP logs must be manually checked and correlated, making frequent audits nearly impossible.
Appsian Provides ERP Defense in Depth A Comprehensive Platform for Adaptive Risk Management
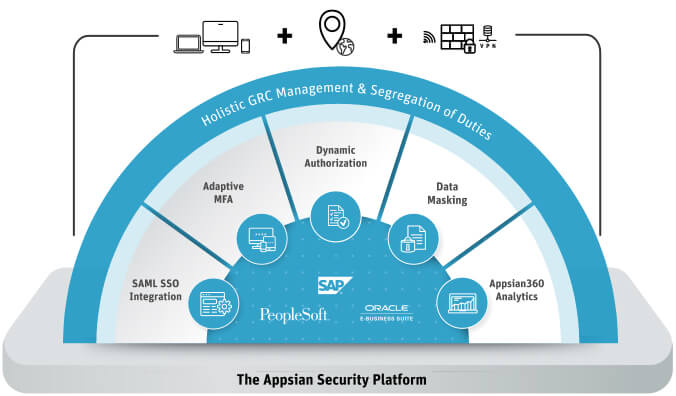
Take a Proactive Approach to Detecting and Preventing Insider Threats
-
ERP Data Access and Usage Monitoring
Appsian Security enables organizations to quickly respond to insider security threats with full forensic information.
-
Enhance Access Controls with Dynamic Authorization Policies
Attribute-based access controls leverage contextual attributes like geolocation, time of day, and IP address to better control the resources users access, how they access them, and from where they access them.
-
Expanded Data Masking
Leverage dynamic data masking and enable data privacy without unnecessary restriction.
-
Step-Up Multi-Factor Authentication
Integrating MFA at the transaction level ensures users only access what is necessary based on their context of access.
Unique Benefits
-

Maximize Your ERP Investment
Modernize legacy applications to meet current business requirements
-
Modernize Risk Management
Enable risk management with greater control and visibility over data access
-

Extend Access Beyond the Firewall
Provide secure, remote access to users using dynamic & fine-grained authentication, authorization & visibility
-

Lightweight & Quick-to-Deploy Solutions
Natively integrated into ERP web server without requiring customizations or additional servers