Stay Secure and Under Control of SAP Authorizations
All SAP authorization requests should be carefully examined and verified that there are no compliance issues before being granted, sensitive authorizations even more so. Therefore, it is crucial to control the authorizations management process and to review authorizations to verify that they are still required periodically.
The security team must always maintain control due to the complexity of authorizations. Certain events, such as granting sensitive permissions or identifying suspicious use of risky authorizations, cannot be ignored and must be taken care of immediately. To address these challenges, Appsian provides a 360° view over authorization and behavior-based security.
Leverage Actual, Real-Time Authorization Usage Data
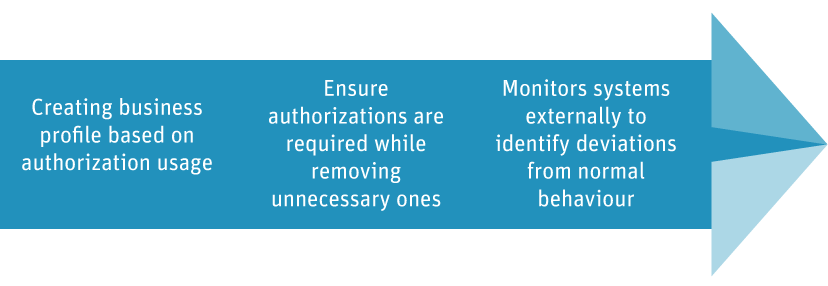
An advanced behavior-based monitoring and analysis solution, Appsian enables enterprises to easily organize, understand and control their user authorizations across ERP systems.
Delivering unprecedented visibility of actual, real-time authorization usage, Appsian performs ongoing monitoring of every user and sends alerts for unusual or unacceptable activity, including risk severity levels.

- “[Appsian] significantly increased the hospital’s security level by eliminating SAP_All authorizations, narrowing authorizations according to actual usage, removing inactive users. We now have real-time insit into the actual SAP-related activities being performed by our employees. The implementation took only 3 weeks, and has reduced the risk of fraud and breach of privacy, months of manual work were avoided, and 18 & has been saved on maintenance cost.”
Rafi Maman- SAP Division Manager
Unique Features
- Externally Installed and non-intrusive to SAP
- Provides complete control over authorization – who should have access and who should not.
- Improves security by eliminating redundant and dormant users, and unused authorizations.
- Queries that recently used sensitive activities and from which terminal.
- Monitors risky objects, sensitive activities, and abnormal behavior.
- Eliminates SAP_ALL and other powerful authorization profiles.
- Receive alerts for unacceptable behavior and sensitive role allocation.