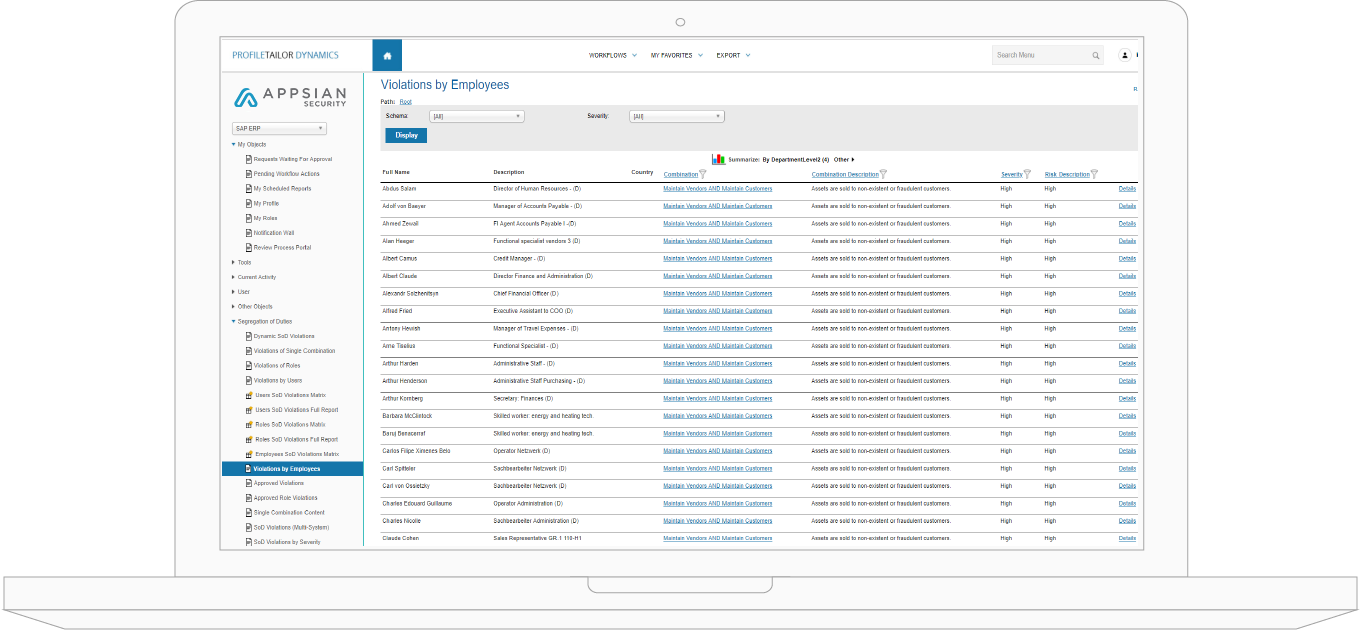
It’s been a period of unprecedented change and adaptation for organizations of all sizes and in every industry over the past 18 months. During this time, I’ve had the opportunity to speak with many of our SAP customers about how they are managing their business risks and protecting their sensitive data. While the topics vary, I’ve noticed a recurring theme: there is a growing—and urgent—interest in using SAP dynamic data masking to strengthen data protection and enforce governance and compliance policies.
But what exactly do we mean by SAP “dynamic” data masking, and what are the best practices for using it to manage business risks and increase data security?
Dynamic Data Masking in SAP Starts with Attribute-Based Access Controls (ABAC)
Data masking is used to protect various types of sensitive and personal data stored in ERP applications, including intellectual property, personally identifiable information (PII), financial data, such as credit card, bank account information, and more. As traditional security perimeters dissolve and compliance requirements increase, protecting your ERP data is of growing importance. This is where dynamic data masking shines. Focused on protecting data at the UI-level in production systems, dynamic data masking can significantly reduce your risk exposure.
A Quick Clarifier: Often, data masking is used in non-production environments to protect ERP data copied from production. This technique is also known as data obfuscation, data scrambling, or data anonymization – and modifies the data itself – meaning it does not work for production systems. Dynamic data masking obfuscates information at the presentation layer (UI-level) without affecting the underlying data (at the database level).
Before dynamic data masking, traditional data masking policies used a static, role-based approach. For example, you include the role(s) and the field(s) in your rules – and a mask is always applied in all circumstances. While it minimized exposure, the static nature limited adoption as it would create barriers to data, and policies would have to be continually updated as users changed roles.
Dynamic data masking extends this policy logic by incorporating attribute-based access controls (ABAC), allowing flexible and wide-reaching rules to be created that incorporate identifiers such as role and other user, data, and access attributes. For example, user’s residency or security clearance, org code, IP address, location, and much more.
Static data masking versus dynamic data masking seems cut and dry. However, my conversations with SAP customers revealed two distinct approaches to using dynamic data masking: One focused on user attributes, and the other focused on the dynamic attributes of access and data itself. While the former allows simple, wide-reaching data masking that addresses functional risk, the latter enables a contextual, risk-based approach that truly balances data security with the needs of the business to access data.
Data Masking Approach #1: Wide-Reaching Policies Based on User Attributes
Many organizations start their data masking journey by analyzing how necessary it is for specific users to see specific data. Focused on functional risk, this approach aligns to least privilege and sets out to mask data that is unnecessary for a user’s job. For example, does a customer service rep need to see the full bank account info on an order? In most cases, no. Or should an HR manager be able to view the PII in a user’s profile from another business unit they are not responsible for? Certainly not.
Using dynamic data masking in these scenarios can deliver wide-reaching policies that incorporate user attributes such as role, business unit, org code, or country of residency. The ABAC technology allows data masking to be enforced “dynamically” when any activity that matches the defined conditions is present. (Meaning there is no need to make changes when users change roles, new users are created, etc.)
This approach is superior compared to the legacy approach that relies on static, role-based policies. Data exposure can quickly be minimized, and from a lifecycle management perspective, ownership is much simpler. However, data is still masked at all times for users, which means the practical scope of usage is still limited.
Data Masking Approach #2: Risk-Based Policies Based on Access Attributes
I’ve recently noticed a shift in thinking from policies based on user attributes towards those based on access attributes. Organizations might be realizing, thanks to the growing number of data privacy regulations and enforcement fines, that their data is now a liability, and they need to implement more risk-based masking policies based more on access attributes than user attributes.
Now an organization can leverage context-aware access controls to mask data in high-risk scenarios and show data in trusted scenarios. For example:
- Masking unpublished financial data from unknown IP addresses/locations
- Masking sensitive business data outside regular working hours
- Masking data for emergency access sessions
A recent use case for this approach to SAP dynamic data masking is on display at a Canadian rail company that needed to provide secure access to sensitive data to a hybrid workforce while also allowing access to self-service SAP modules on mobile devices for their remote workers traveling from city to city and connecting from wherever they have a Wi-Fi connection. They were able to enforce risk-based data masking policies based on access attributes such as location, IP address, time, data sensitivity, and more.
Protecting Data with SAP Dynamic Data Masking Solution
The more I speak with our SAP customers, the more I realize the different “definitions” they have about dynamic data masking. The more accurate definition is that SAP dynamic data masking uses risk-based policies based on access attributes. Without ABAC, companies must enable data masking with extensive customization, resulting in an unscalable ad-hoc solution.
Fortunately, the Appsian Security Platform’s (ASP) dynamic data masking leverages ABAC capabilities to provide fine-grained control over which sensitive data fields can be masked for any specified user in the context of any situation.
I invite you to contact the SAP experts at Appsian to learn how for yourself how we can improve SAP data security and reduce compliance risk with a fully dynamic data masking solution.